Protect your reputation
Authenticate legitimate sending services and block unauthorized mail from bad actors impersonating your organization.
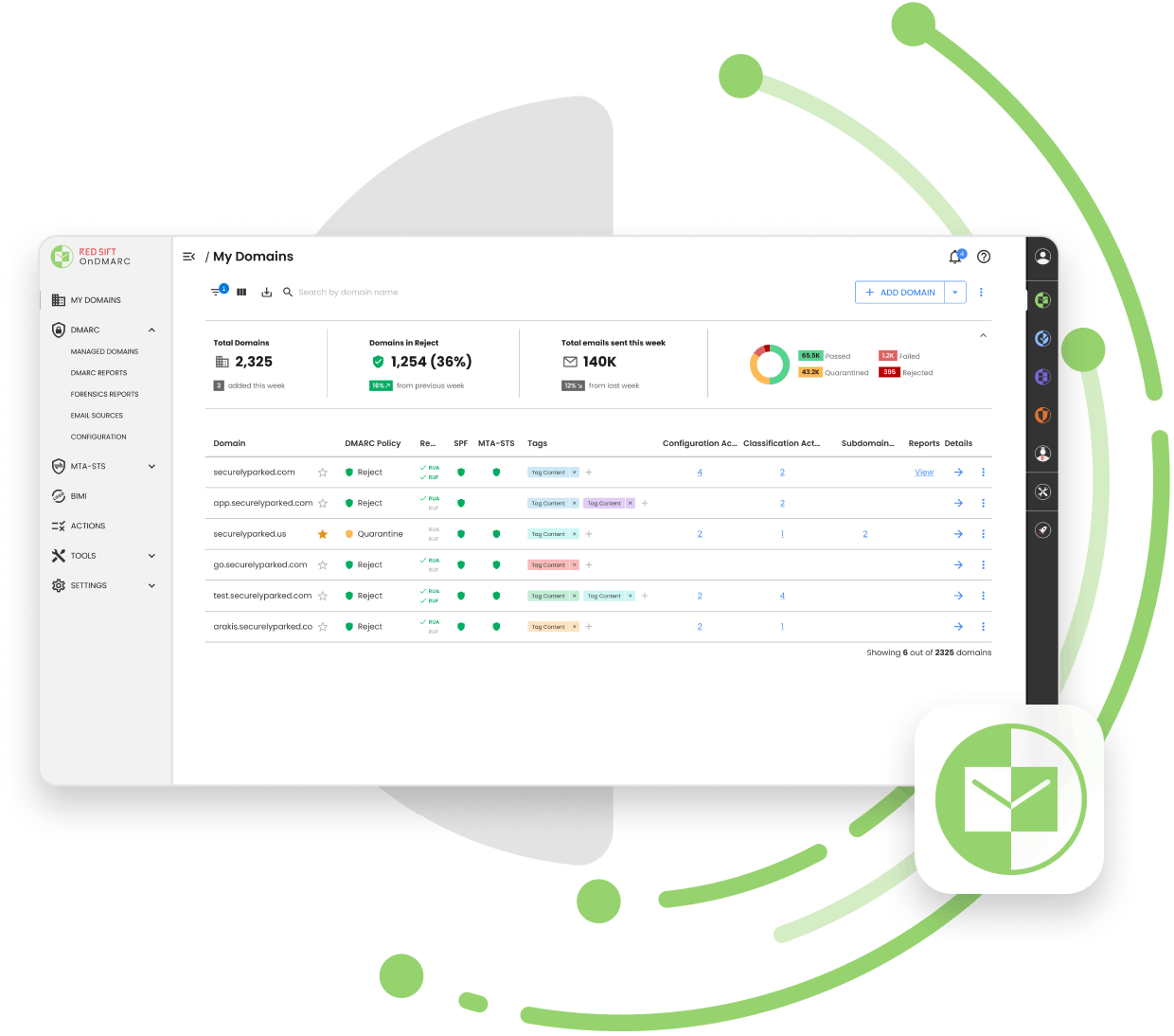

Award-winning, cloud-based DMARC, DKIM and SPF configuration and management.

















































Get to DMARC enforcement safely and efficiently to stop unauthorized use of your email sending domains.
Authenticate legitimate sending services and block unauthorized mail from bad actors impersonating your organization.
See all outbound mail sent from your organization, including third-party providers.
Boost your email deliverability rates by letting receivers know your emails are authenticated.
Comply with email security recommendations made by global government bodies such as NIST, NCSC, and the European Commission.

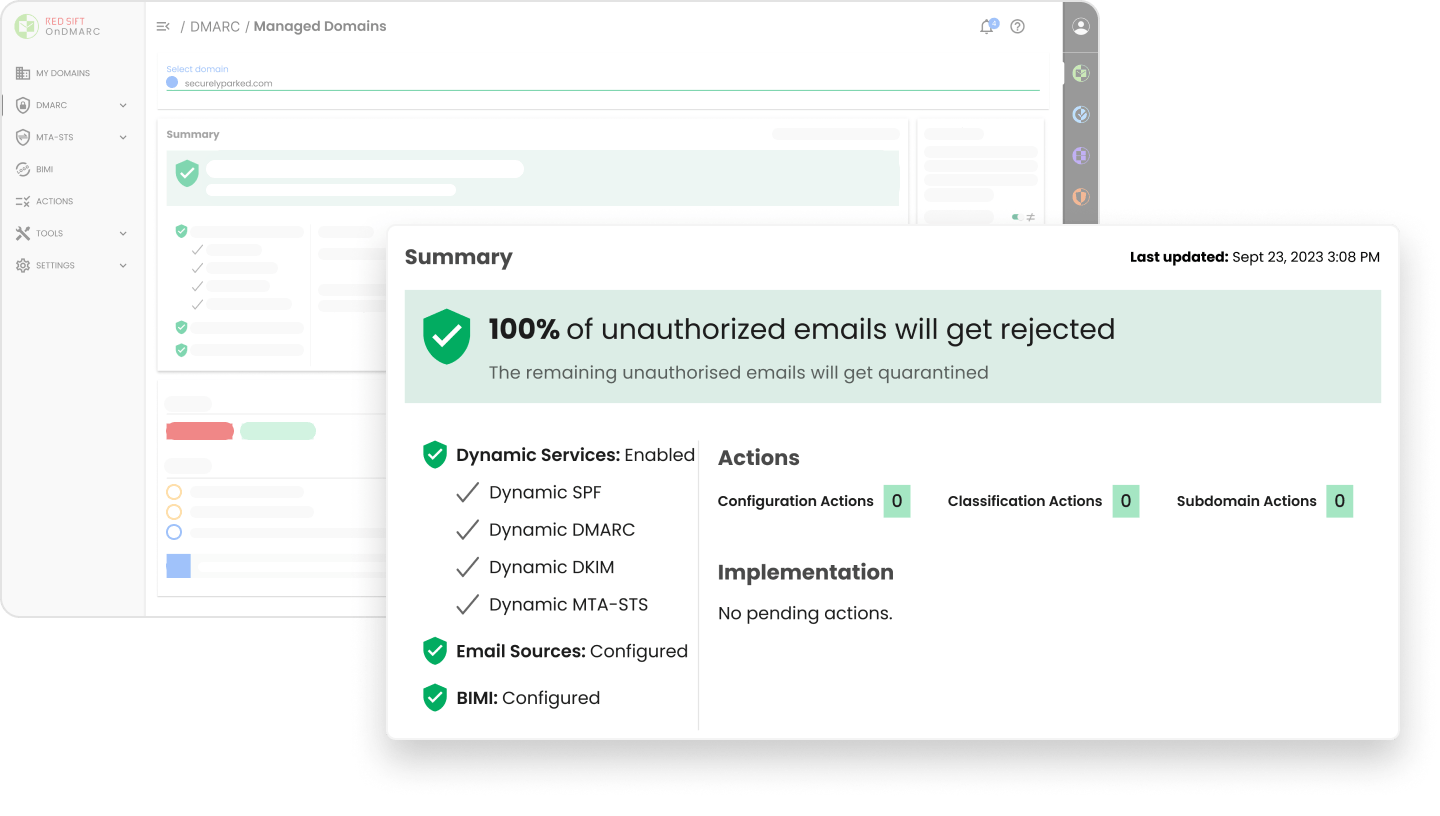
Our customers see a 6-8 week average time to full DMARC enforcement (p=reject or p=quarantine). Our award-winning application helps organizations of all sizes reduce email security risk as efficiently and effectively as possible.
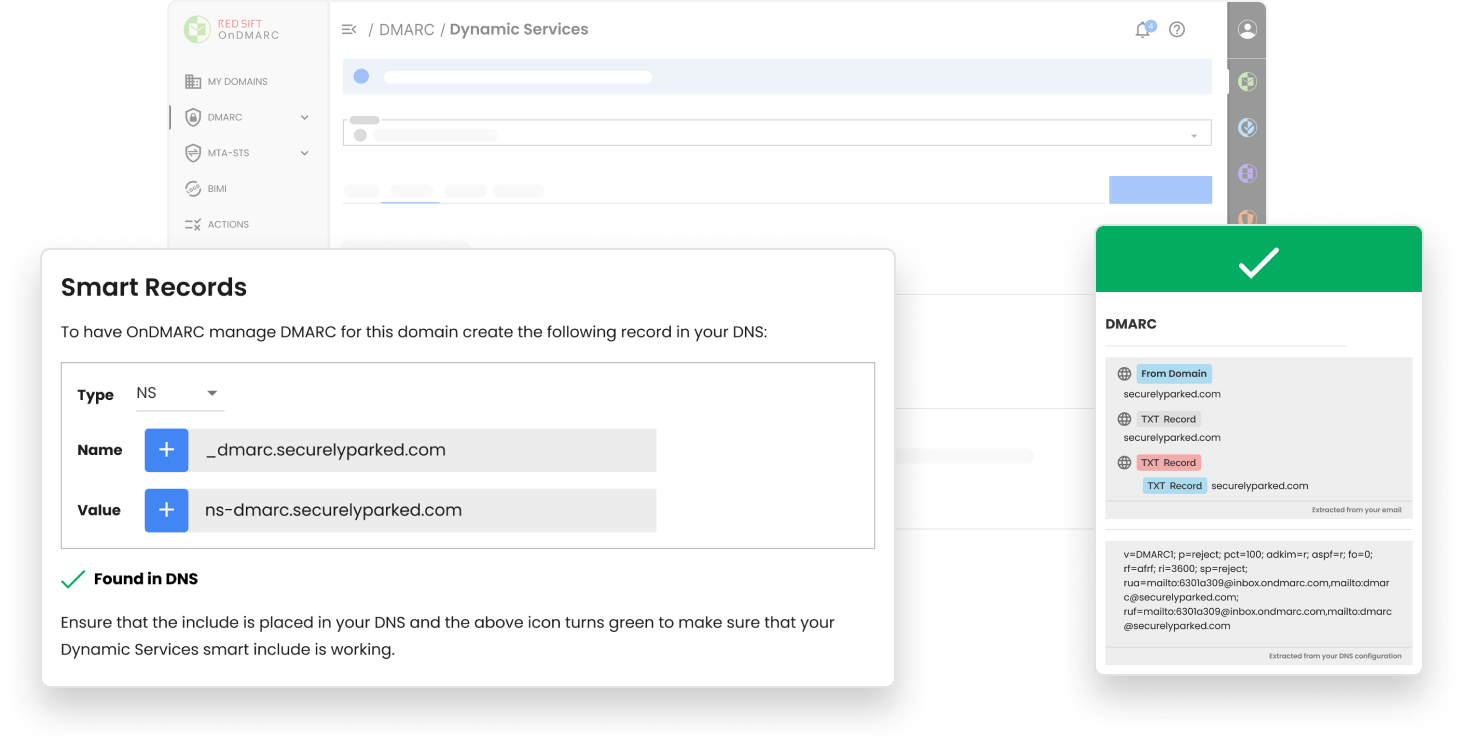
Make a one-time DNS change and manage all of your email authentication from OnDMARC’s UI. Save time, avoid manual configuration errors and quickly add, authenticate or remove services.
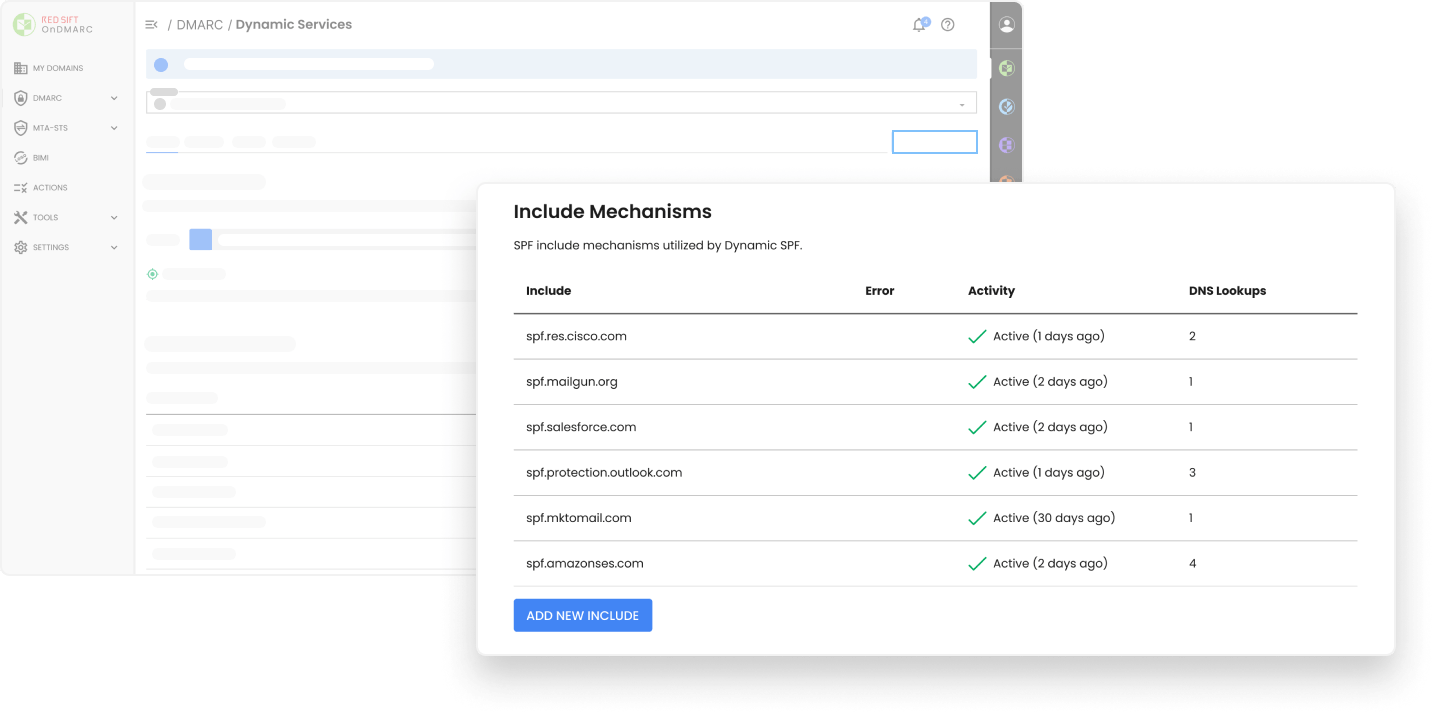
Streamline SPF management and avoid manual DNS changes. No macros means that all legacy email structures, gateways, and receivers will deliver your emails.
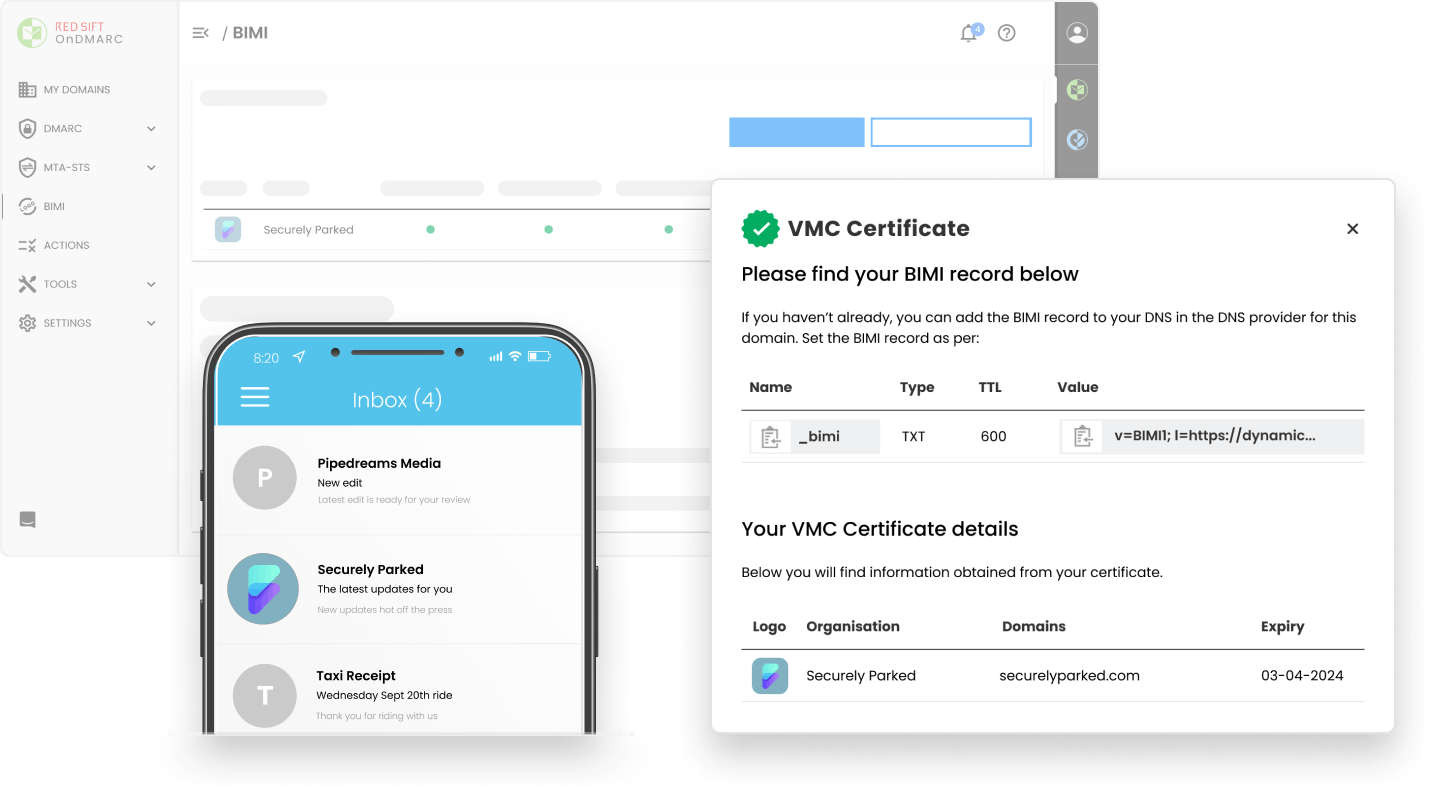
Red Sift OnDMARC is the only BIMI solution on the market with integrated VMC provisioning. Improve open rates by 39% and increase brand recall by 44%.
Learn more about BIMI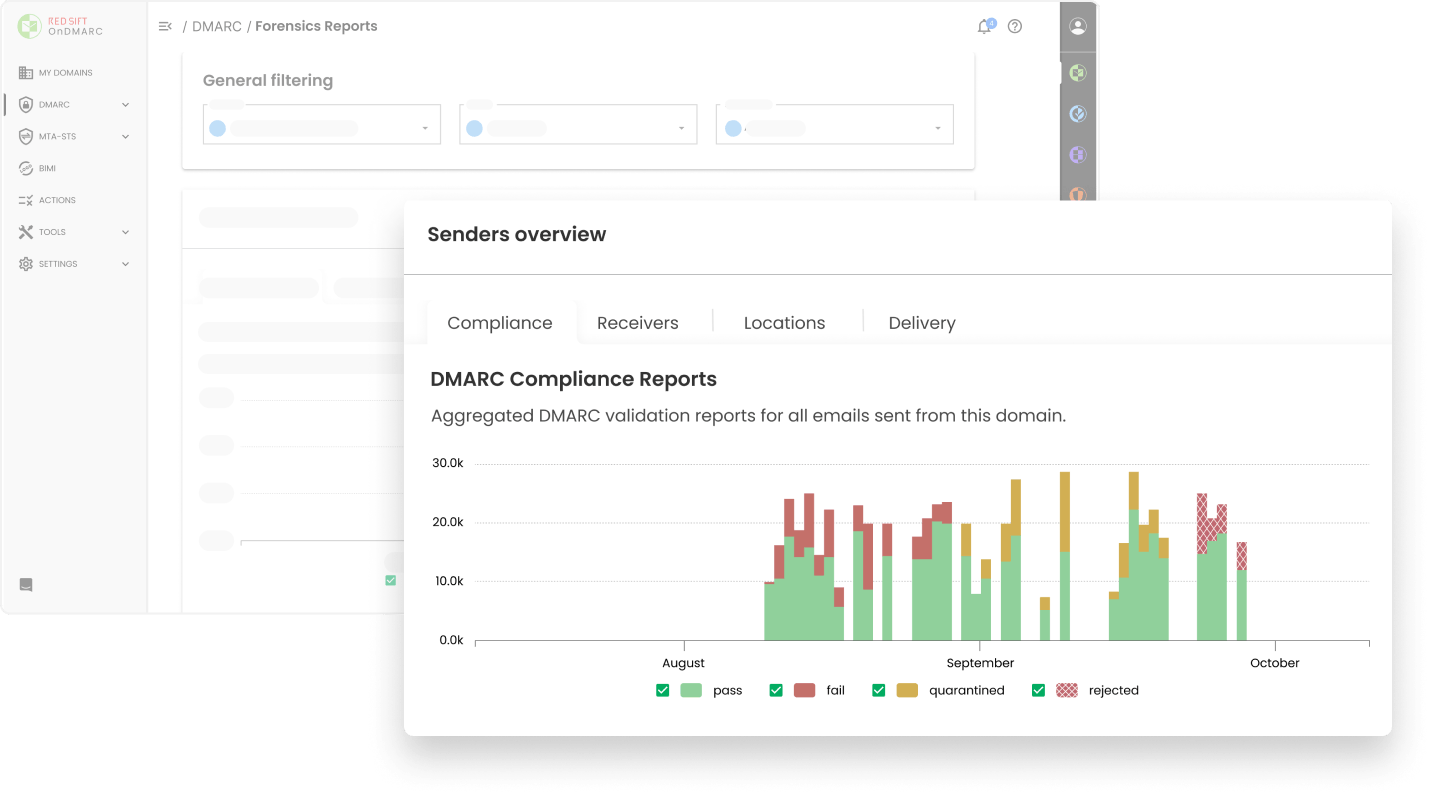
Forensic reporting meets machine learning to deliver granular information about emails that failed DMARC authentication on the receiver side while protecting user privacy.
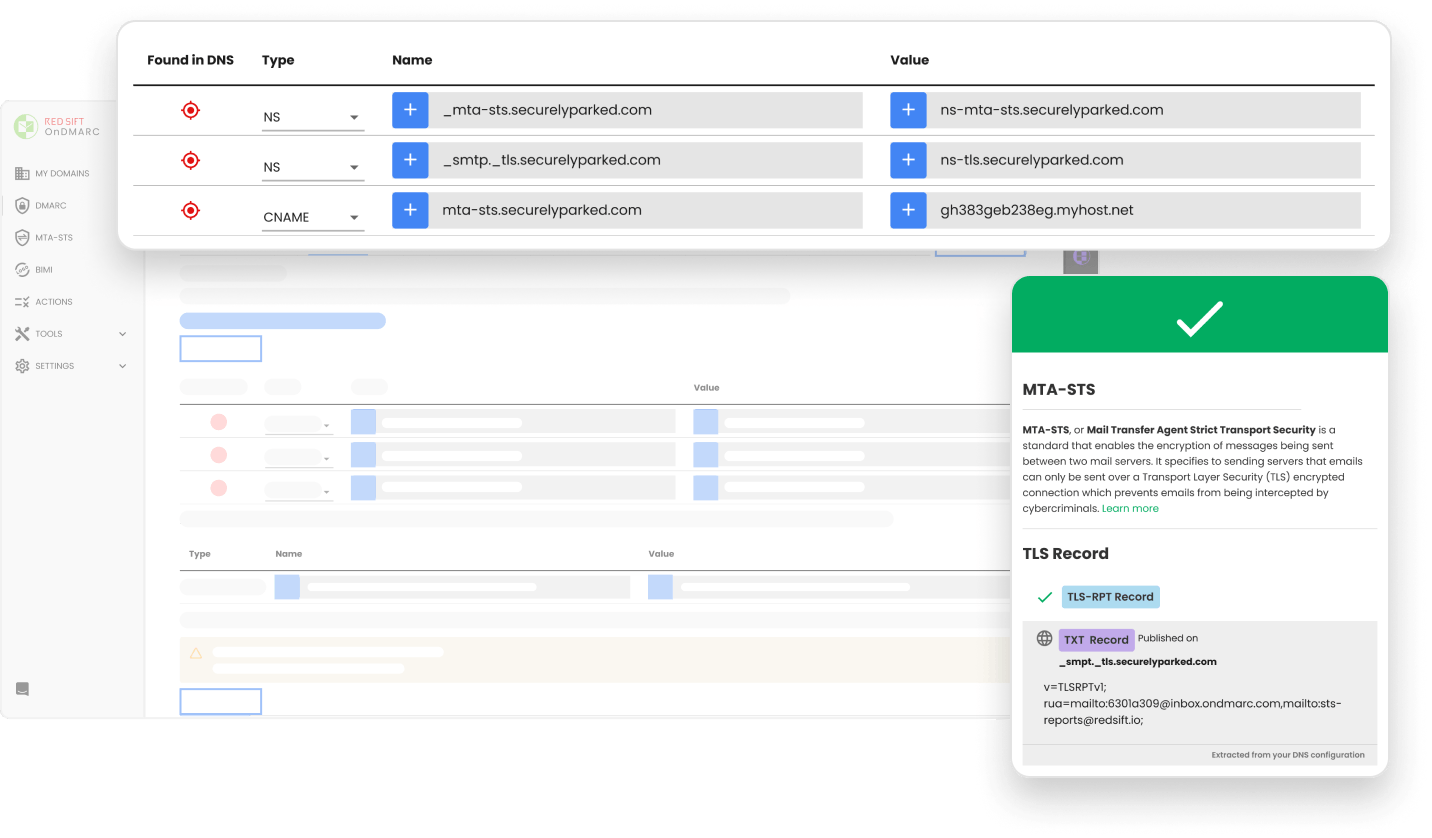
Red Sift OnDMARC makes the deployment of the MTA-STS protocol fast and simple so you can secure your inbound email and prevent intercepted messages.
![[object Object]](https://red-sift.cdn.prismic.io/red-sift/Zh49oDjCgu4jz2CC_RedSift_BrandTextures_PulseLines6.svg?auto=compress,format)
Latest G2 reviews
Unauthorized sending sources successfully blocked

Average email deliverability rate post OnDMARC implementation

Time taken to reach full DMARC compliance on main domains


Manage SPF, DKIM, DMARC, and MTA-STS records from inside the OnDMARC interface without needing to access your DNS.

Easily authenticate SPF across all approved sending services and ensure your organization’s email deliverability is never interrupted.

Streamline and automate the VMC provisioning process to make the journey to BIMI as smooth as possible.

Turn complex forensic DMARC reports into clear, actionable information about your sending sources in order to pinpoint and solve issues within your organization quickly.

Verify if your approved sending services are set up correctly and check them against compliance profiles, including Google & Yahoo bulk sending requirements.

Host the MTA-STS policy file, maintain the SSL certificate, and flag any policy violations through the TLS report to block emails from being intercepted by cybercriminals.
![[object Object]](https://red-sift.cdn.prismic.io/red-sift/07450bf0-7008-41f5-91a9-0ca31822d3da_Quote+Open.svg)

Trusted by the best security leaders in the business





"The diligence and support of the whole OnDMARC team has been second to none. Not only have they got back to us really quickly, they’ve usually seen it before and have an answer. I’ve never felt like I had to do this on my own."

Get to DMARC enforcement safely and efficiently.

Dynamic DMARC, SPF, DKIM & MTA-STS management

Unlimited sending volume per domain

25 domains

Hosted BIMI

Unlimited SPF lookups

User permission management

SIEM & Slack integrations

API access

OnDMARC blocks exact impersonation attacks.
Brand Trust stops lookalike domain impersonation.
Leverage OnDMARC and Brand Trust together to protect your customers, brand, and reputation.
with Investigate


